Difference between revisions of "VPN Access"
m |
(→MacOS (tunnelblick)) |
||
| (35 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | To get full access to our network from external locations we provide a VPN access based on openvpn. This is free software and part of every Linux distribution. The following guide has been tested with Ubuntu | + | To get full access to our network from external locations we provide a VPN access based on openvpn. This is free software and part of every Linux distribution. The following guide has been tested with Ubuntu. |
| + | |||
| + | For Linux we recommend the graphical configuration with [[VPN with Networkmanager]]. | ||
| + | |||
| + | It is available for Windows and MacOS too. | ||
=== Install OpenVPN === | === Install OpenVPN === | ||
| Line 5: | Line 9: | ||
It is not part of the default installation, but can easily installed using apt. Enter the following commands: | It is not part of the default installation, but can easily installed using apt. Enter the following commands: | ||
| − | sudo apt | + | sudo apt install openvpn |
This requires to enter your password to get super user privileges. | This requires to enter your password to get super user privileges. | ||
| Line 11: | Line 15: | ||
=== Command line configuration === | === Command line configuration === | ||
| − | This is | + | We have setup a new VPN gateway. Please use this configuration and report problems. |
| + | |||
| + | This configuration routes all traffic trough ITP. This is useful if you want to download papers, which are restricted to the university network. | ||
| + | The second examples only routes the traffic going directly to the ITP trough the VPN and leaves your default gateway untouched. The only difference is the missing 'redirect-gateway' statement [http://th.physik.uni-frankfurt.de/~thw/vpn/all-via-itp.ovpn] | ||
<pre> | <pre> | ||
client | client | ||
| − | dev | + | dev tun |
proto udp | proto udp | ||
nobind | nobind | ||
| − | remote | + | remote vgw.itp.uni-frankfurt.de |
| − | verify-x509-name | + | verify-x509-name vgw.itp.uni-frankfurt.de name |
remote-cert-tls server | remote-cert-tls server | ||
resolv-retry infinite | resolv-retry infinite | ||
auth-user-pass | auth-user-pass | ||
ca private-ca-itp.crt | ca private-ca-itp.crt | ||
| − | redirect-gateway def1 | + | # Comment this, if you don't want to redirect the default gateway |
| + | redirect-gateway def1 | ||
</pre> | </pre> | ||
Download our CA (Certificate of Authority) [http://th.physik.uni-frankfurt.de/~thw/vpn/private-ca-itp.crt] and store it in the same place. This file is needed for the verification of the authenticity of the server. | Download our CA (Certificate of Authority) [http://th.physik.uni-frankfurt.de/~thw/vpn/private-ca-itp.crt] and store it in the same place. This file is needed for the verification of the authenticity of the server. | ||
| − | + | For only accessing internal services and routing your the normal traffic to your normal uplink use the following configuration: [http://th.physik.uni-frankfurt.de/~thw/vpn/itp.ovpn] | |
| − | |||
<pre> | <pre> | ||
| − | |||
client | client | ||
| − | dev | + | dev tun |
proto udp | proto udp | ||
nobind | nobind | ||
| − | remote | + | remote vgw.itp.uni-frankfurt.de |
| − | verify-x509-name | + | verify-x509-name vgw.itp.uni-frankfurt.de name |
remote-cert-tls server | remote-cert-tls server | ||
resolv-retry infinite | resolv-retry infinite | ||
| Line 45: | Line 51: | ||
ca private-ca-itp.crt | ca private-ca-itp.crt | ||
</pre> | </pre> | ||
| + | |||
=== Start the VPN connection === | === Start the VPN connection === | ||
| Line 71: | Line 78: | ||
Termiate the session by pressing Ctrl-C in this terminal. | Termiate the session by pressing Ctrl-C in this terminal. | ||
| − | === | + | ==OpenVPN for Windows 10== |
| + | |||
| + | At the time of writing, you can download OpenVPN on 'https://openvpn.net/community-downloads/'. | ||
| + | Download the exe-file for Windows 10 and install OpenVPN. | ||
| + | Start 'OpenVPN GUI'. You will get a message that no config file was found. But starting 'OpenVPN GUI' creates a directory to put the config files into. | ||
| + | |||
| + | Next you need to download our CA (Certificate of Authority) [http://th.physik.uni-frankfurt.de/~thw/vpn/private-ca-itp.crt] and the config file [http://th.physik.uni-frankfurt.de/~thw/vpn/all-via-itp.ovpn]. | ||
| + | |||
| + | Some Browsers, depending on the download method, save some of these files as standard text files '.txt'. If this happens, you need to rename them to 'private-ca-itp.crt' and 'all-via-itp.ovpn'. With standard configuration Windows 10 does not show the endings of the file names. The endings are correct if for 'all-via-itp.ovpn' the file type is shown as 'OpenVPN Config' and for 'private-ca-itp.crt' as 'Sicherheitszertifikat' or 'security certificate'. | ||
| + | |||
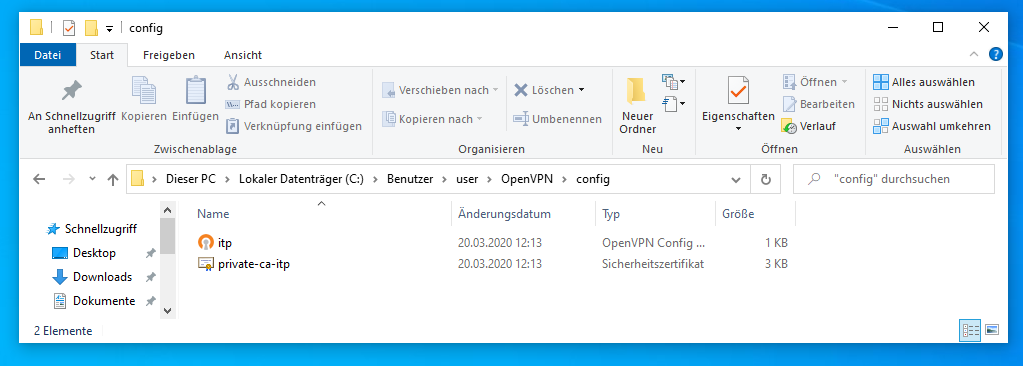
| + | You need to copy/save both files to C:/Users/'yourusername'/OpenVPN/config/, where 'yourusername' is your local username. In the picture below, the directory with the two needed files in it for a german Windows 10 is shown (for the username 'user'). (For both is assumed that 'C' is, as for most Windows systems, your main hard drive.) | ||
| + | |||
| + | [[File:Openvpn-win10-1.png|center]] | ||
| + | |||
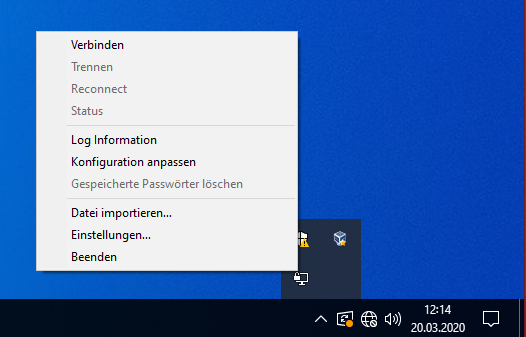
| + | If 'OpenVPN GUI' is started, you can find it in the lower right corner where the minisymbols are. Most likely you need to click on the small arrow first. It is the symbol with the computer screen and the lock symbol. Right click on the symbol and you get a menu where the first option is to connect. Click this option. This menu has less entries if the settings are not found. Then control the previous step. | ||
| + | |||
| + | [[File:Openvpn-win10-2.png|center]] | ||
| + | |||
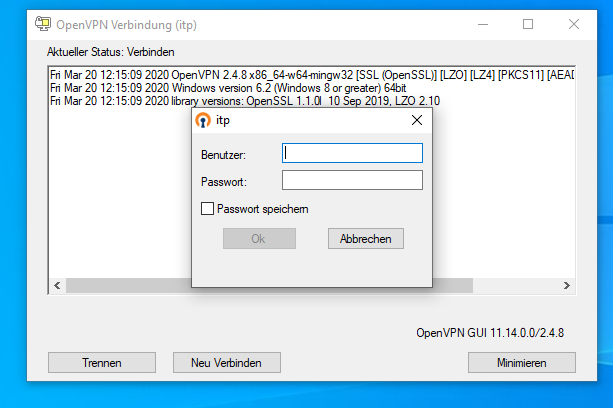
| + | After a few seconds you should get a login screen where you use the credentials of your itp account. | ||
| + | |||
| + | [[File:Openvpn-win10-3.png|center]] | ||
| + | |||
| + | The login takes a few seconds. Your connection was successful if no error window occurs and now the symbol in the lower right is green. | ||
| + | |||
| + | [[File:Openvpn-win10-4.png|center]] | ||
| + | |||
| + | ==MacOS (tunnelblick)== | ||
| + | |||
| + | First download the itp certificate [http://th.physik.uni-frankfurt.de/~thw/vpn/private-ca-itp.crt] and configuration file [http://th.physik.uni-frankfurt.de/~thw/vpn/all-via-itp.ovpn]. If a '.txt' was added to the configuration file name, remove the ending '.txt'. At the end the two files should normally be namend 'private-ca-itp.crt' and 'all-via-itp.ovpn'. | ||
| + | |||
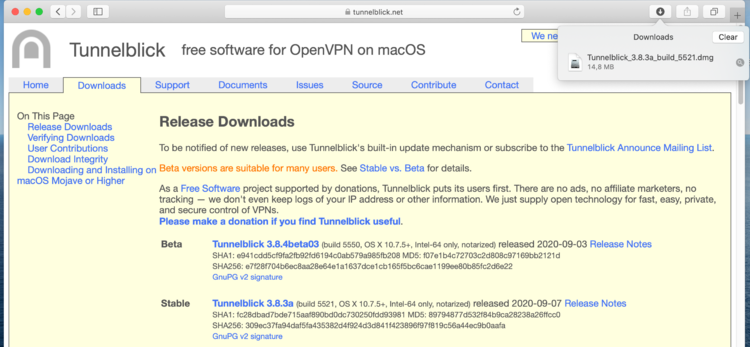
| + | Download the last stable release of the software tunnelblick [https://tunnelblick.net/downloads.html] and execute the dowloaded file. | ||
| + | |||
| + | [[File:Tunnelblick1.png|center|750px]] | ||
| + | |||
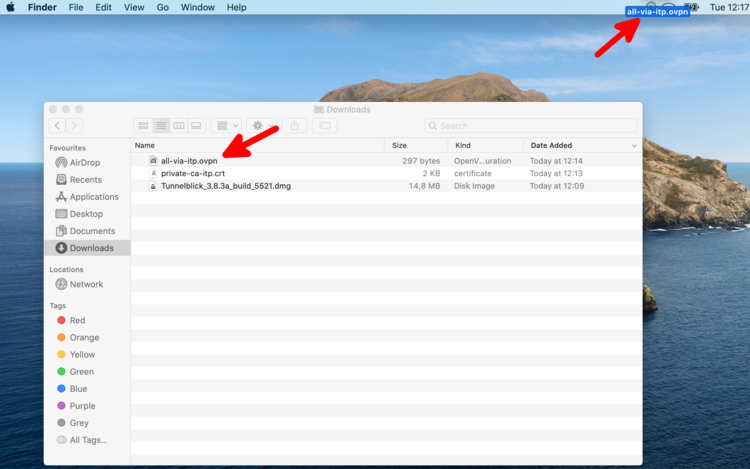
| + | After completion of the installation, a new icon appears in the top bar. Drag and drop the downloaded configuration file to this new icon to add the configuration to tunnelblick. Most likely you do not need to add the certificate manually (it was enough to download it and is handled automatically). Alternatively double-clicking the .ovpn file will also start the import. Both files are copied to system. The original files are no longer referred. | ||
| + | |||
| + | [[File:Tunnelblick2.png|center|750px]] | ||
| + | |||
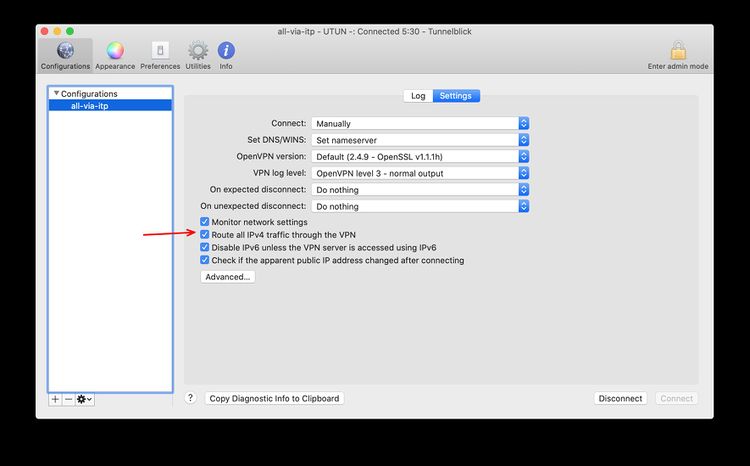
| + | Open the settings page, like shown in the screenshot below and make sure the Default Route Option is selected. This option is ignored from the ovpn configuration. | ||
| + | |||
| + | [[File:Ovpn_settings_default_route.jpg|center|750px]] | ||
| + | |||
| + | Now you can connect to the itp vpn via the new tunnelblick icon. | ||
| + | |||
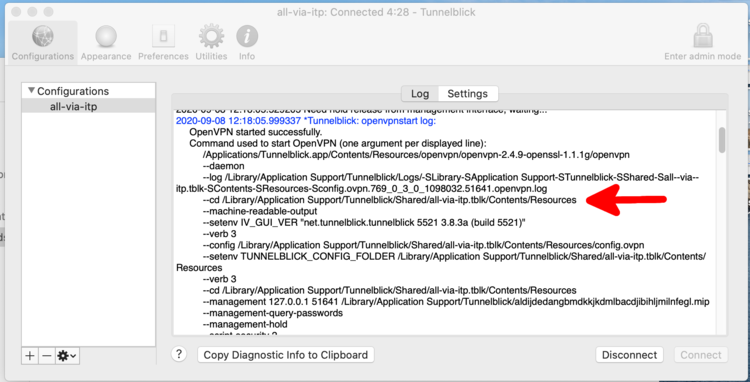
| + | If something fails look into the log of the connection. It also includes multiple times the path to place where the configuration file (tunnelblick automatically renames it into 'config.ovpn') and the certificate are stored. The exact path varies depending on your previous choice to use the configuration just for the current user or for all users. | ||
| + | |||
| + | [[File:Tunnelblick3.png|center|750px]] | ||
| + | |||
| + | In this case the configuration file and the certificate are located in '/Library/Application Support/Tunnelblick/Shared/all-via-itp.tblk/Contents/Resources'. If you need to edit or replace the configuration file or the certificate, this can be done in this directory. If there is just the configuration file in the directory, then copy the certificate to the in the log mentioned directory. | ||
| + | |||
| + | ==Problems changing the vpn settings in tunnelblick (macOS)== | ||
| + | |||
| + | There were problems reported when switching in tunnelblick from the old vpn (vpn.th.physik.uni-frankfurt.de with tap) to the new one (vgw.itp.uni-frankfurt.de with tun). You also have this problem if, after applying the new configuration file itp.ovpn, the vpn does not work and the output contains a line containing 'vpn.th.physik.uni-frankfurt.de'. Search the output for a line beginning with '--config' and ending on '.ovpn'. This line specifies which configuration file (.ovpn) is used to establish the vpn connection and where it is located. Edit this file to have the same content as the itp.ovpn [http://th.physik.uni-frankfurt.de/~thw/vpn/itp.ovpn] (most likely the lines 2, 5 and 6 need to be edited). | ||
| + | |||
| + | ==Warning in tunnelblick (macOS)== | ||
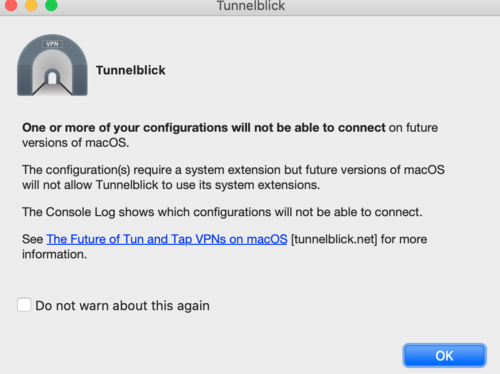
| + | If you get the following warning, you can check the box and click OK. | ||
| + | [[File:Tb-warn.png|center|500px]] | ||
| + | |||
| + | == Replacing the CA Certificate in macOS == | ||
| − | If you | + | When importing the configuration, the crt file is copied to somewhere in the system (see above). If you replace the crt file in your download or whatever folder it will not be used. The simpliest way to fix this is to delete the configuration from Tunnelblick and reimport it. Make sure the option "Route all traffic through the VPN" is checked (see instrcutions above). |
| − | + | This is needed after the replacment of the CA certificate in Nov 2020. This lives for 5 years. Next replacment will be in 2025, if we are still using openVPN then. | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Latest revision as of 16:04, 25 November 2020
To get full access to our network from external locations we provide a VPN access based on openvpn. This is free software and part of every Linux distribution. The following guide has been tested with Ubuntu.
For Linux we recommend the graphical configuration with VPN with Networkmanager.
It is available for Windows and MacOS too.
Contents
Install OpenVPN
It is not part of the default installation, but can easily installed using apt. Enter the following commands:
sudo apt install openvpn
This requires to enter your password to get super user privileges.
Command line configuration
We have setup a new VPN gateway. Please use this configuration and report problems.
This configuration routes all traffic trough ITP. This is useful if you want to download papers, which are restricted to the university network. The second examples only routes the traffic going directly to the ITP trough the VPN and leaves your default gateway untouched. The only difference is the missing 'redirect-gateway' statement [1]
client dev tun proto udp nobind remote vgw.itp.uni-frankfurt.de verify-x509-name vgw.itp.uni-frankfurt.de name remote-cert-tls server resolv-retry infinite auth-user-pass ca private-ca-itp.crt # Comment this, if you don't want to redirect the default gateway redirect-gateway def1
Download our CA (Certificate of Authority) [2] and store it in the same place. This file is needed for the verification of the authenticity of the server.
For only accessing internal services and routing your the normal traffic to your normal uplink use the following configuration: [3]
client dev tun proto udp nobind remote vgw.itp.uni-frankfurt.de verify-x509-name vgw.itp.uni-frankfurt.de name remote-cert-tls server resolv-retry infinite auth-user-pass ca private-ca-itp.crt
Start the VPN connection
Open a terminal and change to the path where the vpn config file is stored. Start the connection with
sudo openvpn itp.ovpn
where itp.ovpn is the name of the config file. openvpn needs root access, therefore you must enter your local password for sudo. After this you have to enter your ITP credentials (Username and Password).
If everything went fine the output will look like:
Fri Dec 7 15:03:00 2012 WARNING: Make sure you understand the semantics of --tls-remote before using it (see the man page). Fri Dec 7 15:03:00 2012 NOTE: OpenVPN 2.1 requires '--script-security 2' or higher to call user-defined scripts or executables Fri Dec 7 15:03:00 2012 UDPv4 link local: [undef] Fri Dec 7 15:03:00 2012 UDPv4 link remote: [AF_INET]141.2.246.2:1194 Fri Dec 7 15:03:00 2012 WARNING: this configuration may cache passwords in memory -- use the auth-nocache option to prevent this Fri Dec 7 15:03:00 2012 [FIAS-ITP_Generic_VPN_Service] Peer Connection Initiated with [AF_INET]141.2.246.2:1194 Fri Dec 7 15:03:02 2012 TUN/TAP device tap0 opened Fri Dec 7 15:03:02 2012 do_ifconfig, tt->ipv6=0, tt->did_ifconfig_ipv6_setup=0 Fri Dec 7 15:03:02 2012 /sbin/ifconfig tap0 10.63.131.1 netmask 255.255.0.0 mtu 1500 broadcast 10.63.255.255 Fri Dec 7 15:03:02 2012 Initialization Sequence Completed
Termiate the session by pressing Ctrl-C in this terminal.
OpenVPN for Windows 10
At the time of writing, you can download OpenVPN on 'https://openvpn.net/community-downloads/'. Download the exe-file for Windows 10 and install OpenVPN. Start 'OpenVPN GUI'. You will get a message that no config file was found. But starting 'OpenVPN GUI' creates a directory to put the config files into.
Next you need to download our CA (Certificate of Authority) [4] and the config file [5].
Some Browsers, depending on the download method, save some of these files as standard text files '.txt'. If this happens, you need to rename them to 'private-ca-itp.crt' and 'all-via-itp.ovpn'. With standard configuration Windows 10 does not show the endings of the file names. The endings are correct if for 'all-via-itp.ovpn' the file type is shown as 'OpenVPN Config' and for 'private-ca-itp.crt' as 'Sicherheitszertifikat' or 'security certificate'.
You need to copy/save both files to C:/Users/'yourusername'/OpenVPN/config/, where 'yourusername' is your local username. In the picture below, the directory with the two needed files in it for a german Windows 10 is shown (for the username 'user'). (For both is assumed that 'C' is, as for most Windows systems, your main hard drive.)
If 'OpenVPN GUI' is started, you can find it in the lower right corner where the minisymbols are. Most likely you need to click on the small arrow first. It is the symbol with the computer screen and the lock symbol. Right click on the symbol and you get a menu where the first option is to connect. Click this option. This menu has less entries if the settings are not found. Then control the previous step.
After a few seconds you should get a login screen where you use the credentials of your itp account.
The login takes a few seconds. Your connection was successful if no error window occurs and now the symbol in the lower right is green.
MacOS (tunnelblick)
First download the itp certificate [6] and configuration file [7]. If a '.txt' was added to the configuration file name, remove the ending '.txt'. At the end the two files should normally be namend 'private-ca-itp.crt' and 'all-via-itp.ovpn'.
Download the last stable release of the software tunnelblick [8] and execute the dowloaded file.
After completion of the installation, a new icon appears in the top bar. Drag and drop the downloaded configuration file to this new icon to add the configuration to tunnelblick. Most likely you do not need to add the certificate manually (it was enough to download it and is handled automatically). Alternatively double-clicking the .ovpn file will also start the import. Both files are copied to system. The original files are no longer referred.
Open the settings page, like shown in the screenshot below and make sure the Default Route Option is selected. This option is ignored from the ovpn configuration.
Now you can connect to the itp vpn via the new tunnelblick icon.
If something fails look into the log of the connection. It also includes multiple times the path to place where the configuration file (tunnelblick automatically renames it into 'config.ovpn') and the certificate are stored. The exact path varies depending on your previous choice to use the configuration just for the current user or for all users.
In this case the configuration file and the certificate are located in '/Library/Application Support/Tunnelblick/Shared/all-via-itp.tblk/Contents/Resources'. If you need to edit or replace the configuration file or the certificate, this can be done in this directory. If there is just the configuration file in the directory, then copy the certificate to the in the log mentioned directory.
Problems changing the vpn settings in tunnelblick (macOS)
There were problems reported when switching in tunnelblick from the old vpn (vpn.th.physik.uni-frankfurt.de with tap) to the new one (vgw.itp.uni-frankfurt.de with tun). You also have this problem if, after applying the new configuration file itp.ovpn, the vpn does not work and the output contains a line containing 'vpn.th.physik.uni-frankfurt.de'. Search the output for a line beginning with '--config' and ending on '.ovpn'. This line specifies which configuration file (.ovpn) is used to establish the vpn connection and where it is located. Edit this file to have the same content as the itp.ovpn [9] (most likely the lines 2, 5 and 6 need to be edited).
Warning in tunnelblick (macOS)
If you get the following warning, you can check the box and click OK.
Replacing the CA Certificate in macOS
When importing the configuration, the crt file is copied to somewhere in the system (see above). If you replace the crt file in your download or whatever folder it will not be used. The simpliest way to fix this is to delete the configuration from Tunnelblick and reimport it. Make sure the option "Route all traffic through the VPN" is checked (see instrcutions above).
This is needed after the replacment of the CA certificate in Nov 2020. This lives for 5 years. Next replacment will be in 2025, if we are still using openVPN then.